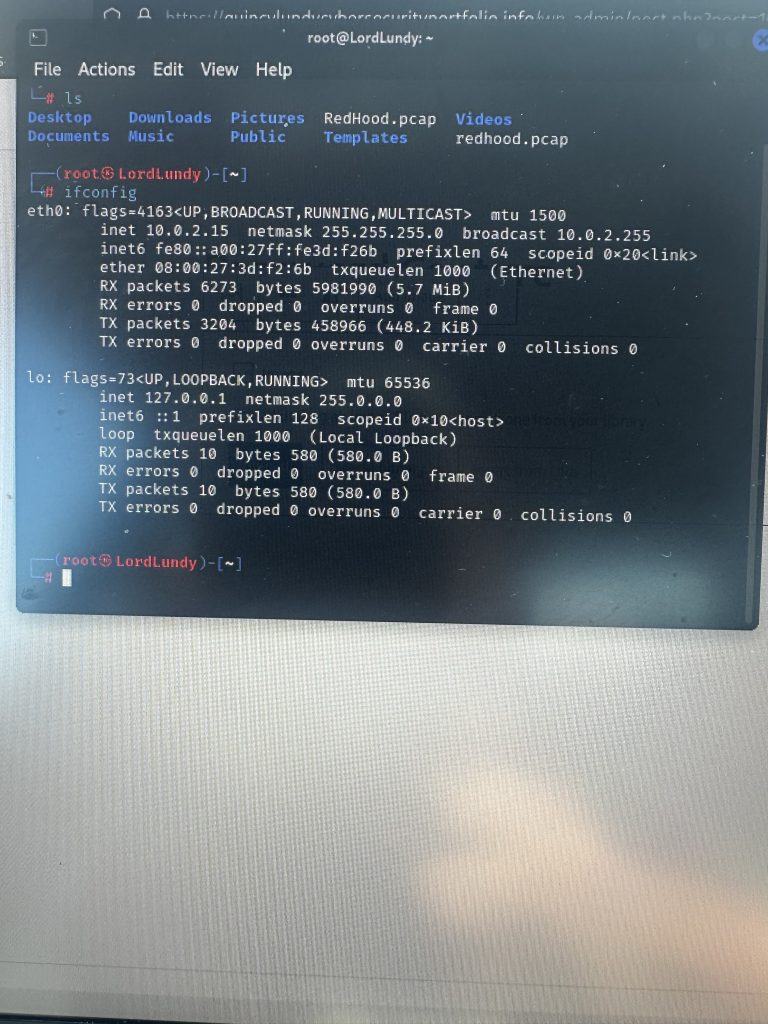
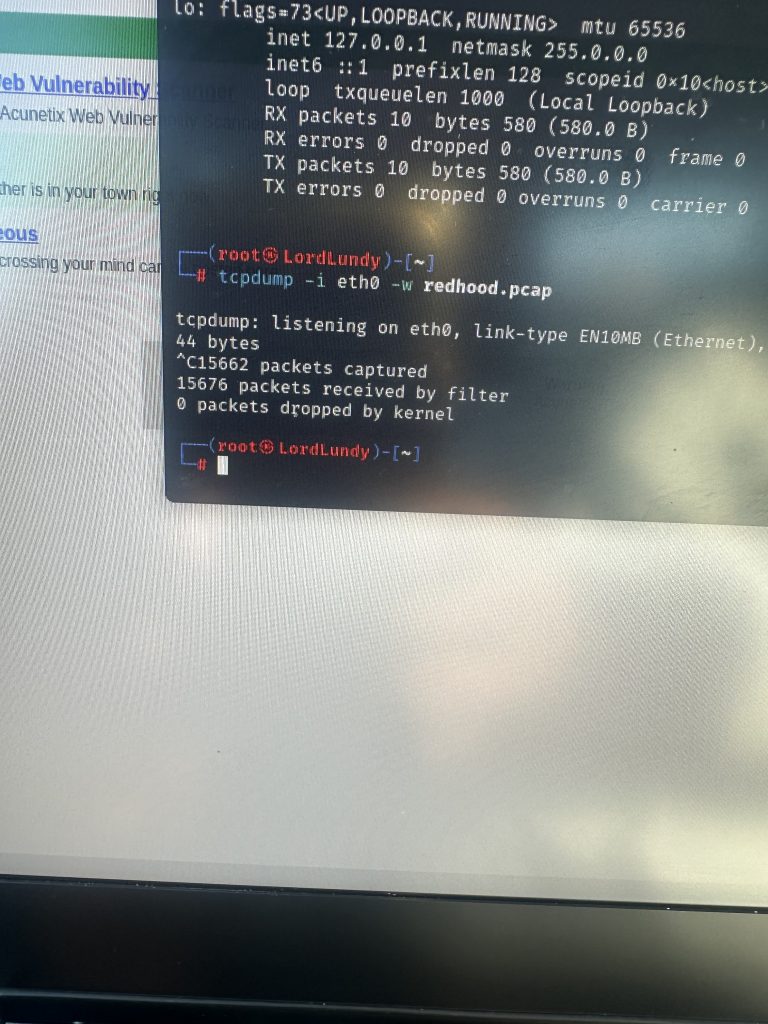
I ran ifconfig to identify which interface was doing the outbound communicating which was eth0
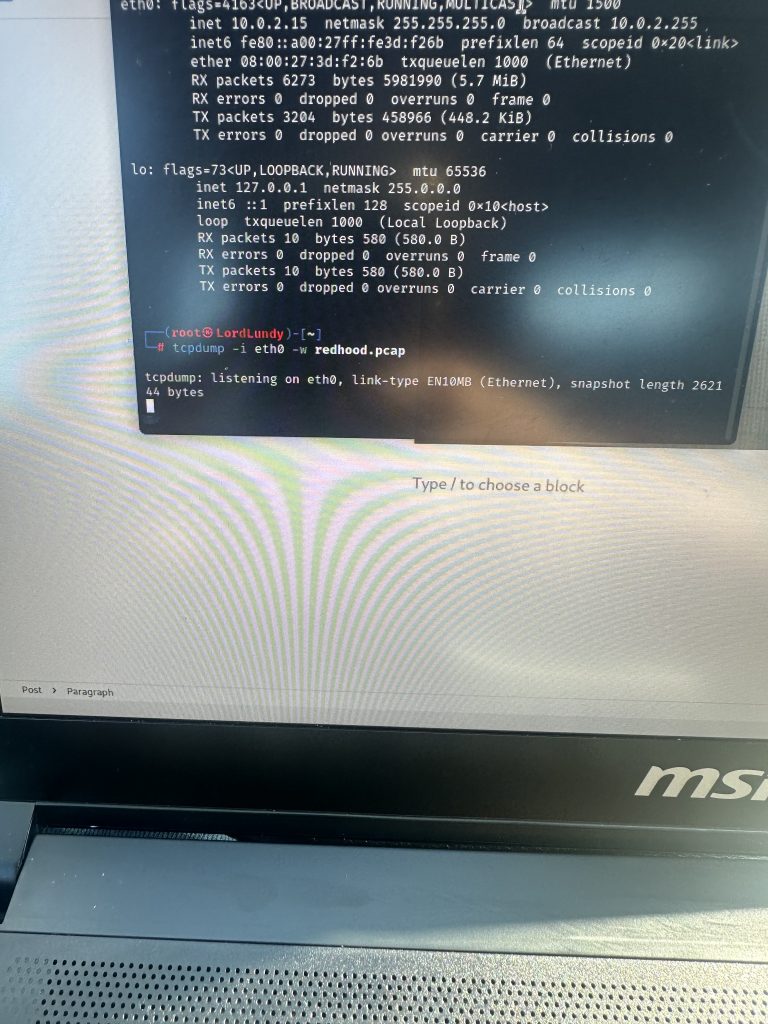
I ran a tcpdump and directed the traffic to a pcap file I created
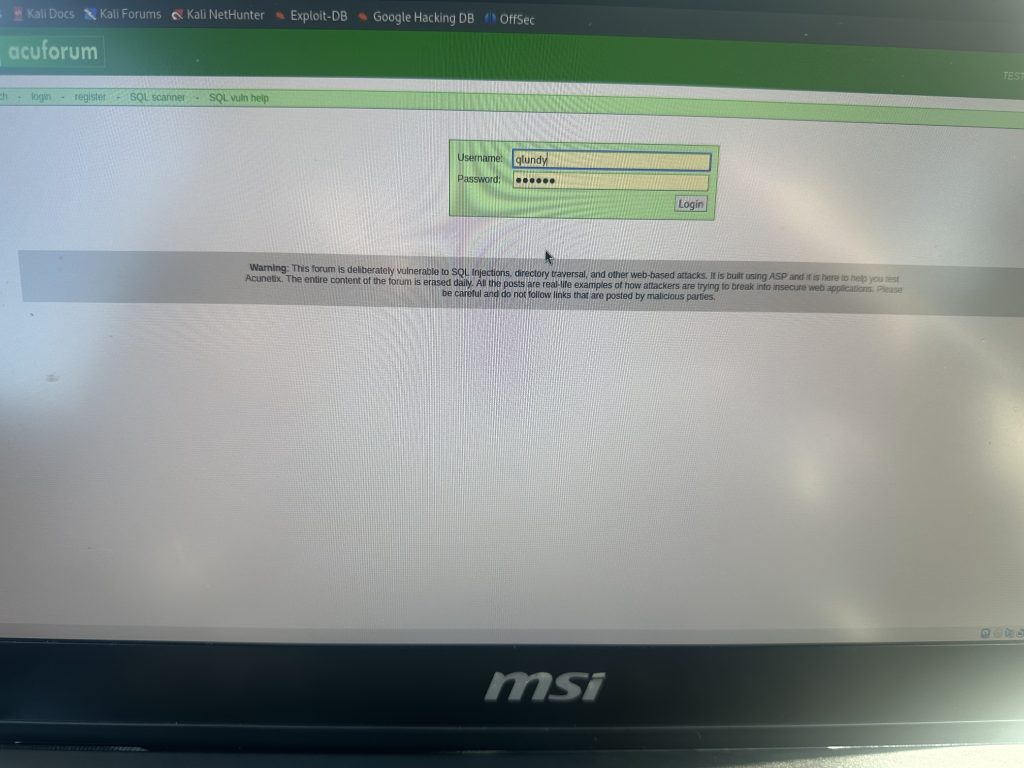
I logged into profile with plain text password
I closed out the packet capture
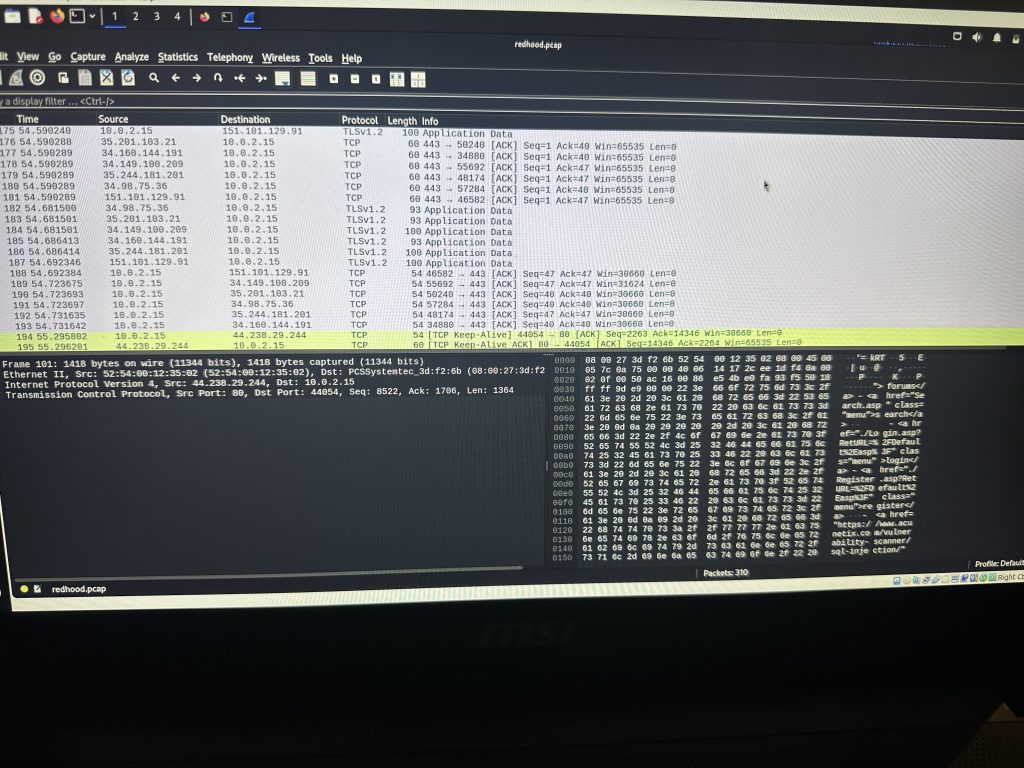
Using wireshark I analyzed the contents in the pcap file
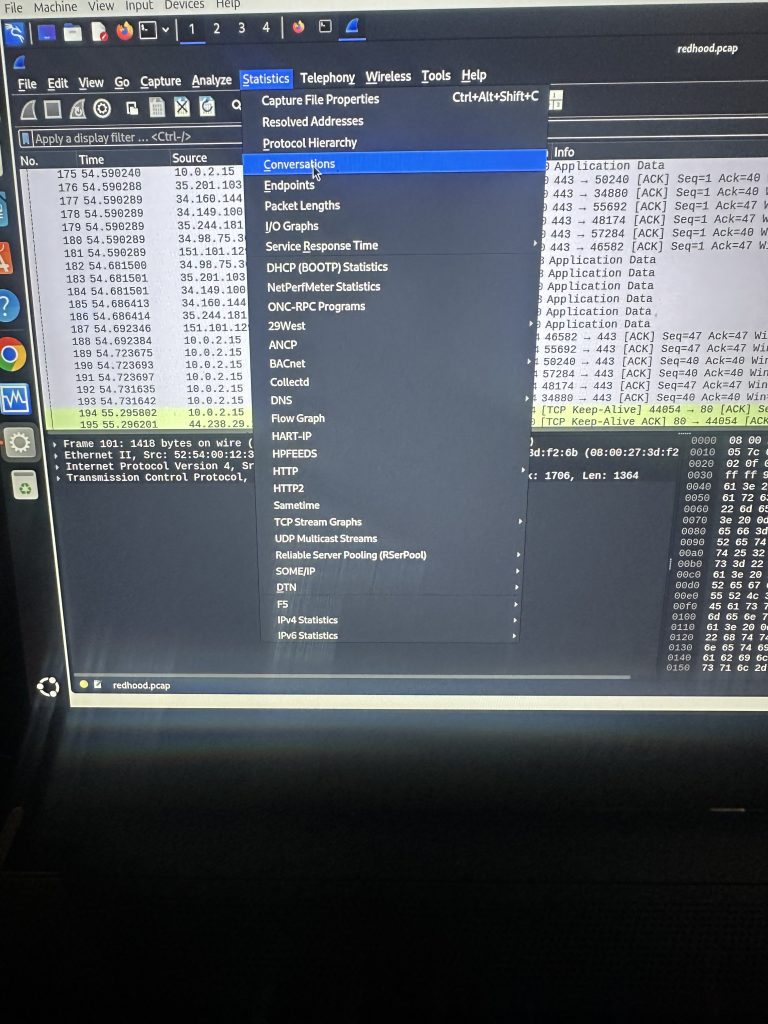
I went to the statistics tab and selected conversations to get an overview of all the specific connections
I found the connection with most packets and selected it
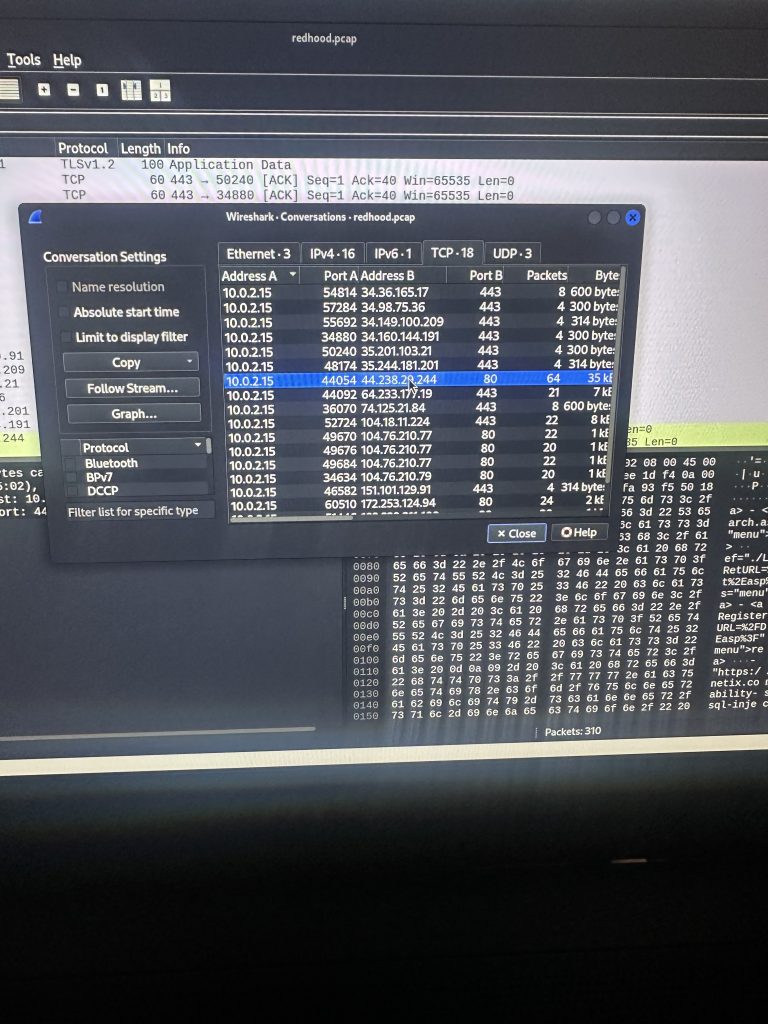
I right clicked to filter the bidirectional traffic between the two addresses
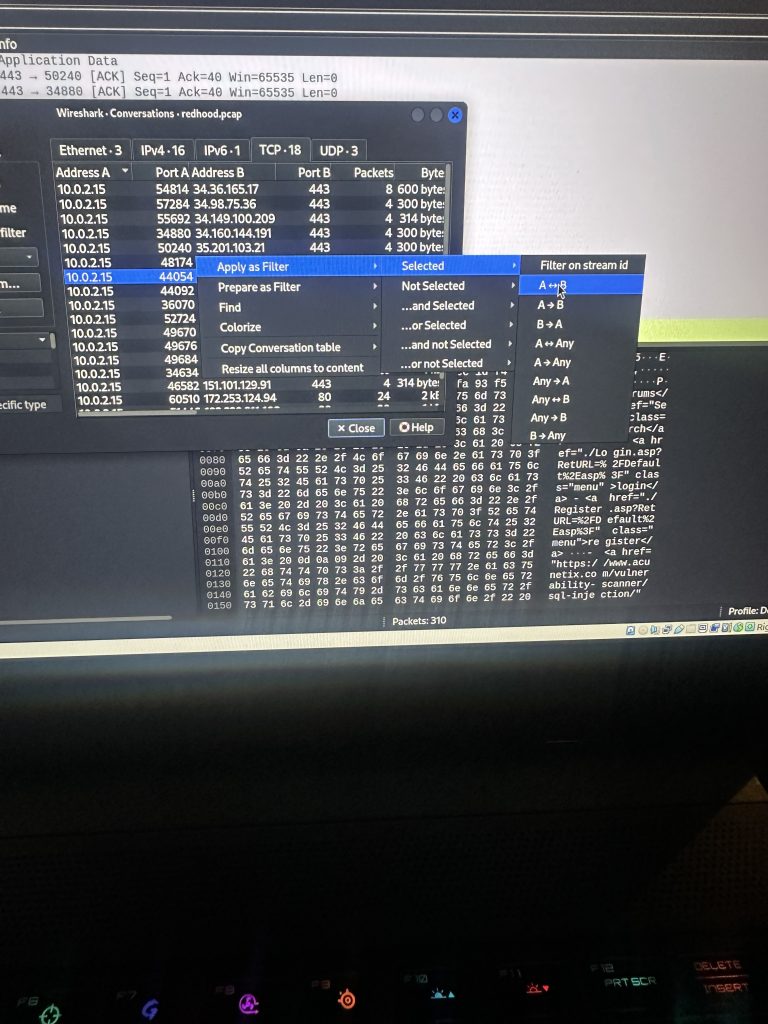
The filter button gave a list of all the traffic between the two addresses
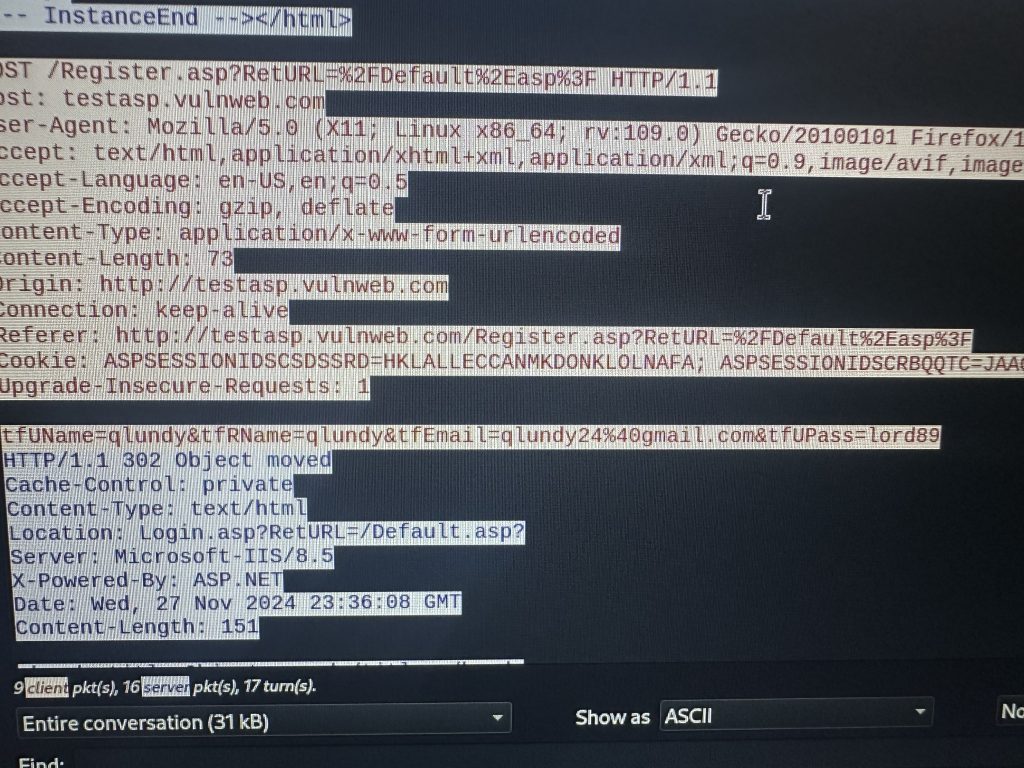
now if I go through each one of these eventually I will be able to capture my password But …
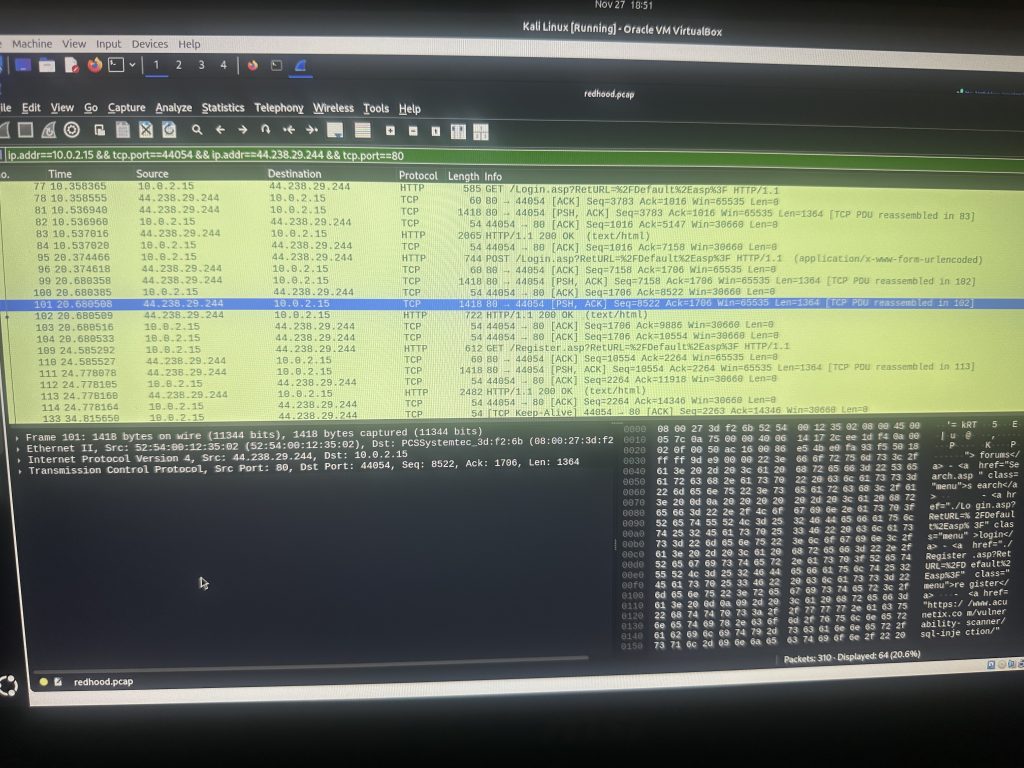
If tcpdump contains “password” as you can see it gives me the ones I need without me having to go through all of that.
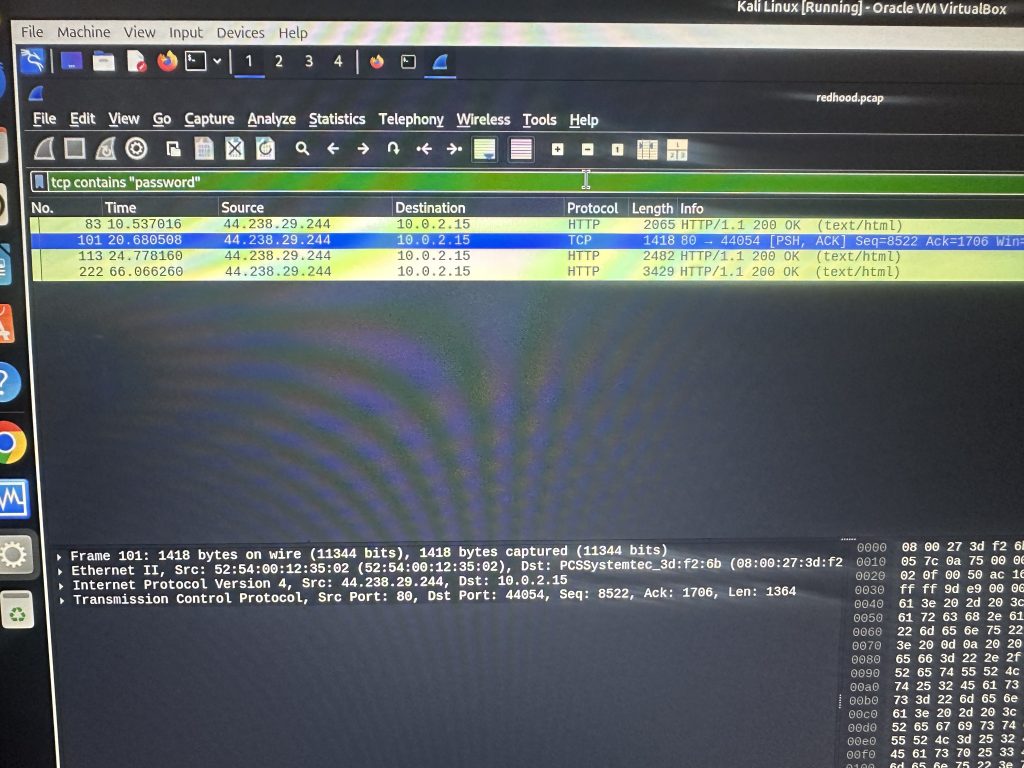
I right clicked hit follow to get the tcp stream
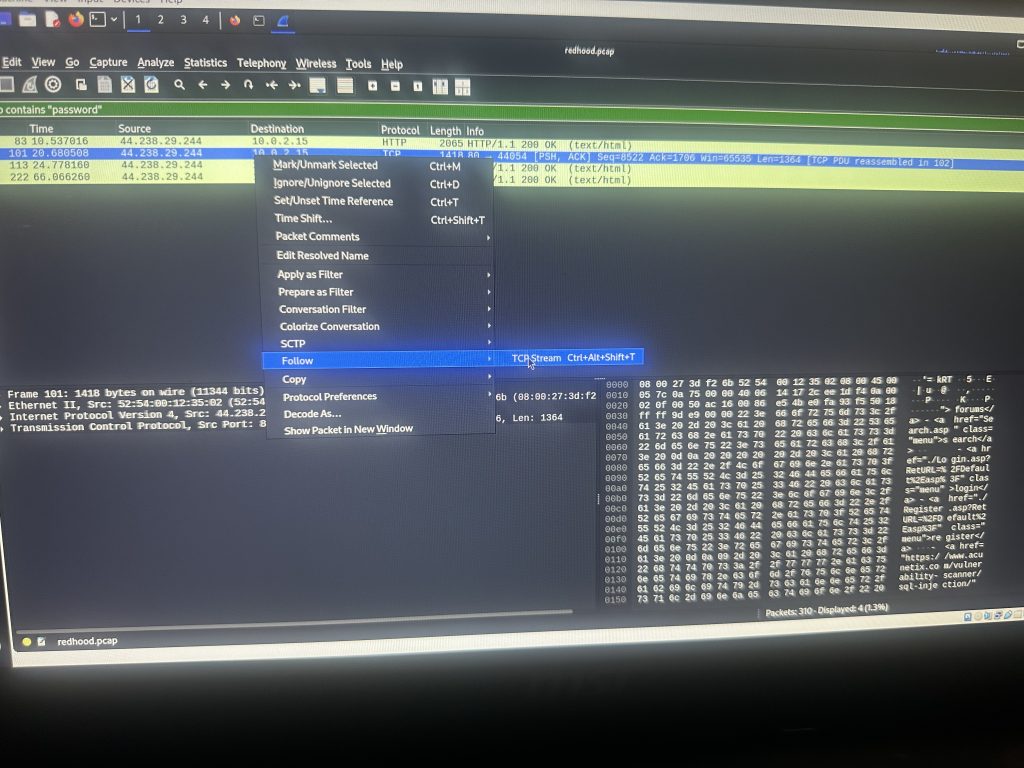
One you click the stream it brings you here to this screen and if you look closely ….
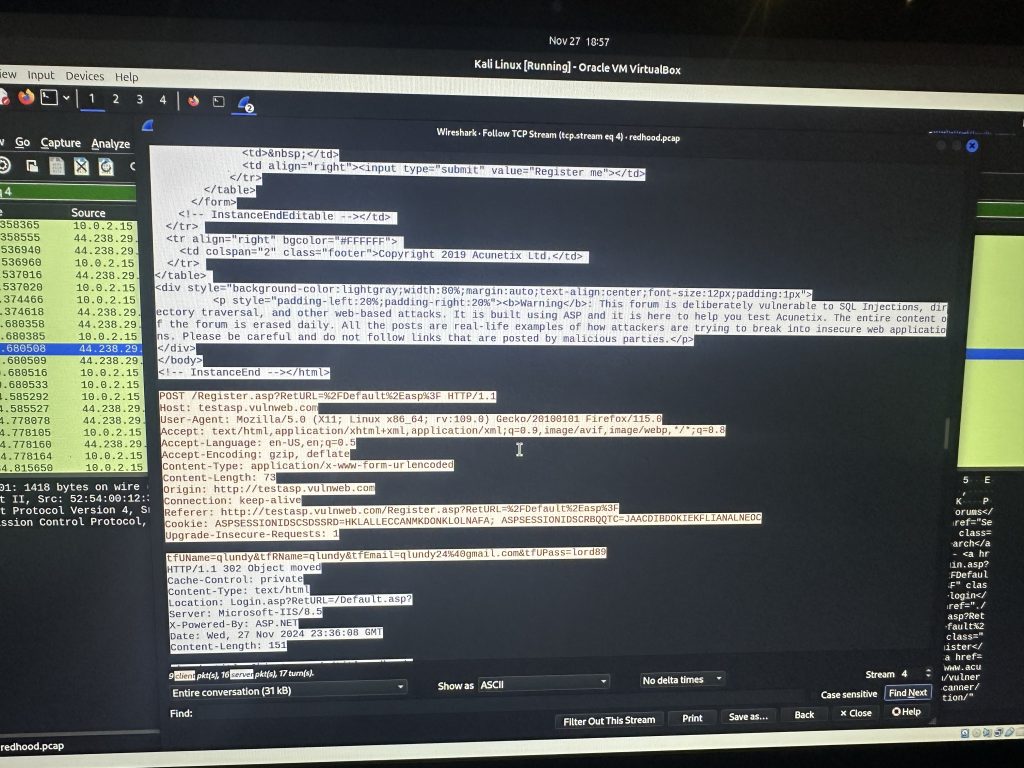
You will find the password and other login info !!!